PQSecure-SW™
High-Assurance Post-Quantum Cryptography Software
PQSecure-SW™ delivers production-grade, side-channel-aware, formally verified post-quantum cryptography software for embedded systems, secure boot, Root-of-Trust, defense platforms, and silicon-integrated deployments.
Our modular software stack includes:
- libpqsecure-C – High-assurance portable C implementation
- libpqsecure-rs – Memory-safe pure Rust implementation
- libpqsecure-asm – Architecture-optimized assembly acceleration layer
Together, they provide portable, high-performance, quantum-safe cryptography engineered for real-world deployment.
✅ Algorithms Supported
PQSecure-SW™ implements finalized NIST standards, forthcoming standards, stateful hash-based signatures, and classical primitives required for hybrid deployments.
NIST Post-Quantum Standards
- ✅ FIPS 203 – ML-KEM
- ✅ FIPS 204 – ML-DSA
- ✅ FIPS 205 – SLH-DSA (SPHINCS+)
- ✅ FIPS 206 – FN-DSA (Falcon) (available soon)
- ✅ FIPS 202 – SHA-3 (Keccak)
Stateful Hash-Based Signatures
- ✅ RFC 8391 – XMSS
- ✅ RFC 8554 – LMS
- ✅ NIST SP 800-208 – Stateful Hash-Based Signatures
Classical Hash Standards
- ✅ RFC 6234 – SHA-2, HMAC, HKDF
All implementations support relevant NIST security levels (1, 3, 5 where applicable) and are engineered for embedded, aerospace, defense, 5G, IoT, secure elements, and supply-chain-assured silicon deployments.
Background: Transition to Post-Quantum Cryptography
With the publication of FIPS 203, 204, 205, and the upcoming FIPS 206, the migration from RSA and ECC to quantum-safe cryptography has entered full deployment. Federal mandates (including CNSA 2.0 guidance) require adoption of NIST-standardized PQC algorithms in secure communications, firmware authentication, and Root-of-Trust systems.
Secure deployment requires more than algorithm compliance. It requires:
- ✅ Constant-time implementations
- ✅ Side-channel-aware design
- ✅ Formal verification
- ✅ Stack-aware embedded optimization
- ✅ Hardware integration readiness
PQSecure-SW™ is engineered specifically for these high-assurance environments.
Software Stack Architecture
🔷 libpqsecure-C
High-assurance portable C implementation optimized for firmware, RTOS, secure boot, and silicon integration.
Key Features
- ✅ Pure C implementation
- ✅ Formally verified using CBMC
- ✅ Strict constant-time discipline
- ✅ Stack-optimized variants
- ✅ ACVP-tested infrastructure
- ✅ Portable across major toolchains
- ✅ Designed for bare-metal, RTOS, and embedded Linux
🔷 libpqsecure-rs
Memory-safe Rust implementation designed for embedded and security-critical deployments.
Key Features
- ✅ Pure Rust implementation
- ✅
no_stdsupport - ✅ Formally verified using Kani
- ✅ Strict constant-time design
- ✅ Memory-safe by construction
- ✅ ACVP-tested infrastructure
- ✅ Portable across Linux, macOS, Windows, RISC-V, ARM Cortex-M
🔷 libpqsecure-asm
Architecture-specific assembly acceleration layer delivering maximum performance on constrained MCUs and high-performance processors.
Optimized Backends
- ✅ ARM Cortex-M3
- ✅ ARM Cortex-M4 / M33
- ✅ ARM Cortex-A series
- ✅ RISC-V (RV32 / RV64)
- ✅ x86-64
Capabilities
- ✅ Optimized NTT implementations
- ✅ Modular arithmetic acceleration
- ✅ Polynomial multiplication acceleration
- ✅ SHA acceleration (where supported)
- ✅ Strict constant-time assembly primitives
- ✅ DSP instruction utilization (M4/M33)
- ✅ Optional vector acceleration (AVX2 / NEON)
libpqsecure-asm integrates seamlessly with both libpqsecure-C and libpqsecure-rs.
Code-Size Configuration Options
PQSecure-SW™ supports two deployment profiles:
🚀 Large Variant (Performance Optimized)
- ✅ Maximum throughput
- ✅ Stack-optimized implementations
- ✅ Three ML-DSA sign stack/performance tradeoffs
- ✅ Ideal for embedded Linux, gateways, defense systems
🔒 Small Variant (Low Stack Footprint)
- ✅ Reduced stack usage
- ✅ Lower performance than Large variant
- ✅ Ideal for constrained MCUs and secure elements
Formal Verification & Assurance
PQSecure-SW™ integrates formal methods directly into production cryptographic software.
- ✅ Rust verified using Kani
- ✅ C verified using CBMC
- ✅ Constant-time coding discipline
- ✅ Side-channel-aware implementation
- ✅ ACVP testing infrastructure
- ✅ Designed for FIPS-oriented validation pathways
Continuous Integration & Embedded Validation
PQSecure-SW™ includes production-grade CI infrastructure:
- ✅ Linux / macOS / Windows testing
- ✅ RISC-V and ARM via QEMU
- ✅ On-board embedded validation
- ✅ Automated regression testing
CI Architecture (Option 3)
- ✅ board-repo → hardware execution
- ✅ crypto-repo → OS + QEMU validation
- ✅ crypto-board-repo → automated cloning + board regression
Why PQSecure-SW™
PQSecure-SW™ is engineered specifically for:
- ✅ Embedded environments
- ✅ Secure boot & Root-of-Trust
- ✅ Defense & aerospace systems
- ✅ Silicon integration
- ✅ Hardware / software co-design
We combine:
- ✅ NIST compliance
- ✅ Formal verification
- ✅ Constant-time discipline
- ✅ Assembly-level optimization
- ✅ Embedded portability
- ✅ Hardware acceleration readiness
to deliver production-ready, high-assurance quantum-safe cryptography.
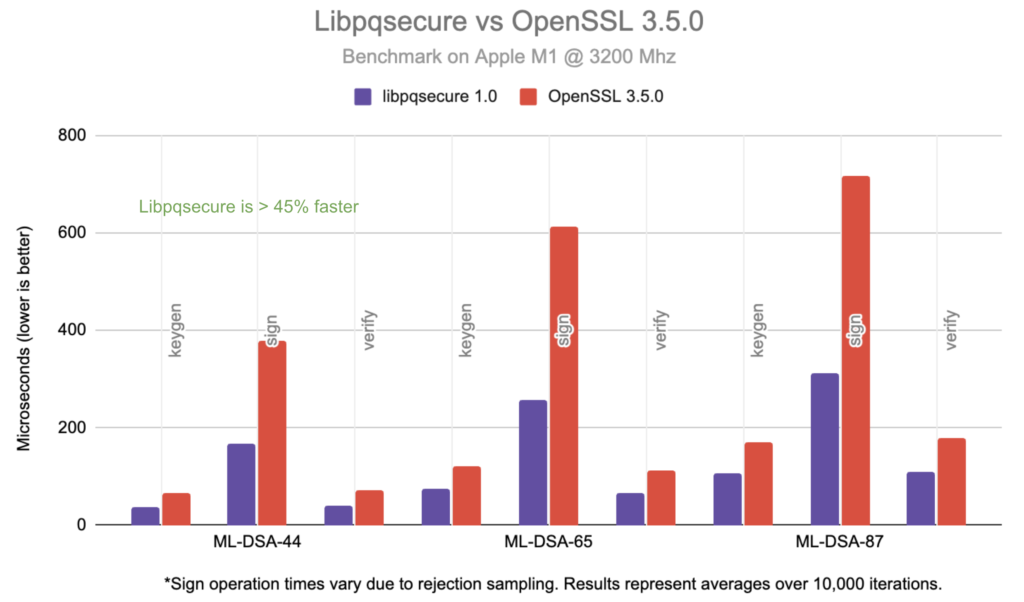
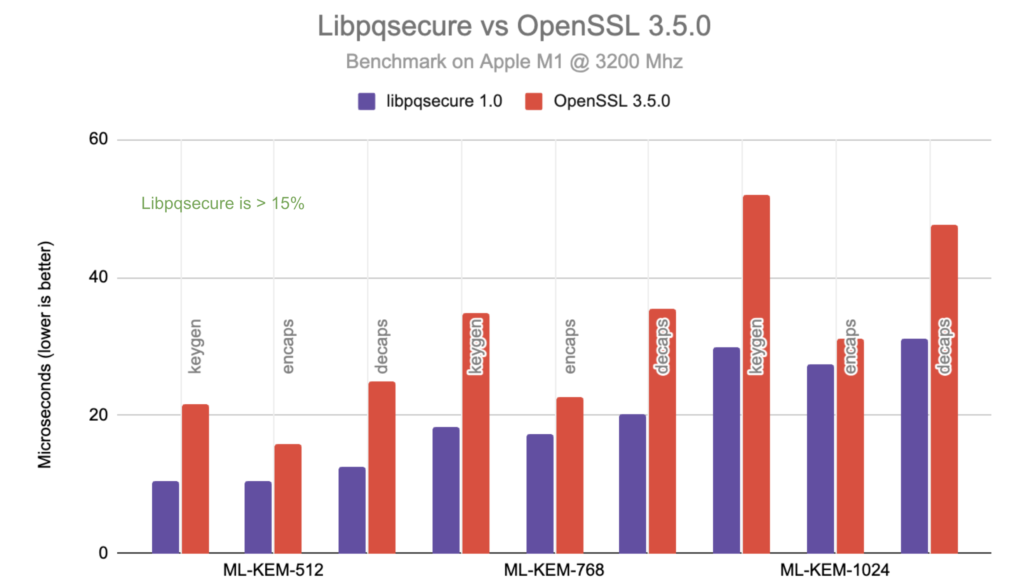
Sample Performance Benchmark Results & Comparisons
The above benchmarks compare libpqsecure 1.0 against OpenSSL 3.5.0 on an Apple M1 processor @ 3.2 GHz. Results are reported in microseconds (lower is better).
Across all tested parameter sets of FIPS 203 (ML-KEM) and FIPS 204 (ML-DSA), libpqsecure consistently demonstrates measurable performance advantages.
ML-KEM (FIPS 203)
- libpqsecure shows >15% lower latency across key generation, encapsulation, and decapsulation.
- Performance gains increase with higher security levels (ML-KEM-768 and ML-KEM-1024).
- Optimized NTT and polynomial arithmetic pipelines contribute to reduced execution time.
ML-DSA (FIPS 204)
- libpqsecure achieves >45% faster signing performance compared to OpenSSL.
- Verification and key generation also show consistent improvements.
- Optimizations include constant-time arithmetic, stack-aware tuning, and reduced memory movement.
Note: ML-DSA signing performance reflects average results over 10,000 iterations due to rejection sampling variability.
These results demonstrate that PQSecure-SW™ is not only standards-compliant and formally verified, but also engineered for high-performance production deployments.
NIST CAVP/ACVP Compliance/Certifications
libpqsecure-c
libpqsecure-rust